In a World of Risks, How Secure is Your Data?
- ServiceIT+

- Oct 1, 2024
- 2 min read
Updated: Apr 3, 2025

How Secure is Your Organization’s Sensitive Data in the Age of Cyber Threats?
As remote work becomes the standard, employees access company systems from various locations—coffee shops, home offices, and even remote cabins. While this flexibility enhances productivity, it also creates new security challenges. Organizations must ensure their sensitive data remains protected, even as cyber threats become more advanced. Traditional security measures, such as VPNs and firewalls, are no longer enough to safeguard against sophisticated attacks, making it essential to adopt a more dynamic approach.
The solution lies in iBoss Zero Trust Secure Access Service Edge (SASE). With cyber threats evolving daily, iBoss ensures that trust is continuously verified, not assumed. Every user, device, and access request undergoes strict validation, guaranteeing that only authorized individuals can access sensitive resources. By making data and applications invisible to unauthorized users, iBoss significantly reduces the risk of breaches, ransomware, and data leaks.
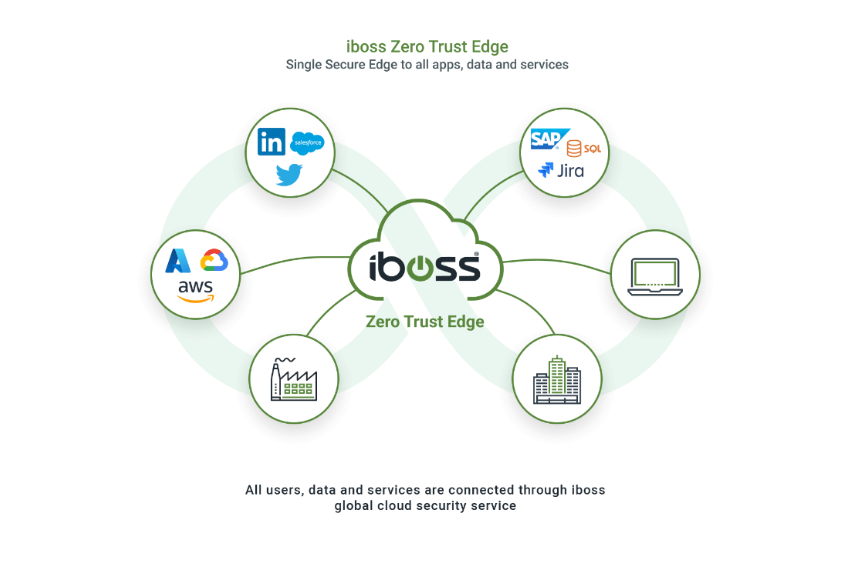
But iBoss doesn’t just protect data—it revolutionizes how security is managed across your network. Here’s how:
Resource Mapping
Understanding where sensitive data is stored and who has access is critical to security. iBoss provides complete visibility by mapping data locations and access permissions, allowing organizations to enforce tighter control and prevent unauthorized exposure. With a clear view of your data landscape, you can implement stronger security policies without disrupting daily operations.
Seamless Access Without VPN Hassles
Traditional security models rely on VPNs, which can be slow and cumbersome for employees working remotely. iBoss eliminates the need for VPNs, enabling direct, secure access to applications and data. This streamlines workflows, enhances productivity, and ensures users experience minimal disruptions. Employees can work efficiently, while security teams maintain strict control over access points.
Multi-Layered Advanced Security
Basic security measures, like password protection, are no longer sufficient. iBoss inspects every access request with multiple layers of validation, analyzing behavior patterns and identifying potential threats in real time. If an access attempt appears suspicious, iBoss can immediately deny entry or request further verification. This proactive approach minimizes security risks and prevents unauthorized users from infiltrating your network.
Real-Time Threat Monitoring
Cybersecurity isn’t just about setting up defenses—it’s about continuous vigilance. iBoss monitors all access points and user activities in real time, instantly detecting suspicious behavior. This real-time oversight allows organizations to respond to threats before they escalate, reducing downtime and financial losses caused by cyberattacks.
Balancing Security and Productivity
A common challenge organizations face is balancing strong security with seamless user experience. Security measures shouldn’t slow down operations. iBoss ensures employees have smooth access to critical resources while maintaining a high level of protection. With its intelligent authentication process, security remains robust without disrupting workflows.
At ServiceIT+, we specialize in implementing iBoss solutions tailored to your organization’s unique needs. Our team of experts will guide you through a seamless transition, ensuring you unlock the full potential of iBoss without interfering with daily operations.
Protect your sensitive data today. Inquire at inquiries@serviceitplus.com to discover how iBoss can enhance your security posture in an era of evolving cyber threats.




